Recent Articles
Quickest Mobile Data Recovery Case: 100% of Data Recovered in One Hour
How to fix a corrupted database on PS4
How to Troubleshoot Black or Blank Screens in Windows
LockBit Ransomware: A Comprehensive Guide to the Most Prolific Cyber Threat
How To Use iPad Recovery Mode
How to Prevent Overwriting Files: Best Practices
External Hard Drive Not Showing Up On Windows – Solved
How to Fix a Corrupted iPhone Backup
Backup and Remote Wiping Procedures
Common VMware Issues and Troubleshooting Solutions

I think there's an issue with my storage device, but I'm not sure Start a free evaluation →
I need help getting my data back right now Call now (800) 972-3282
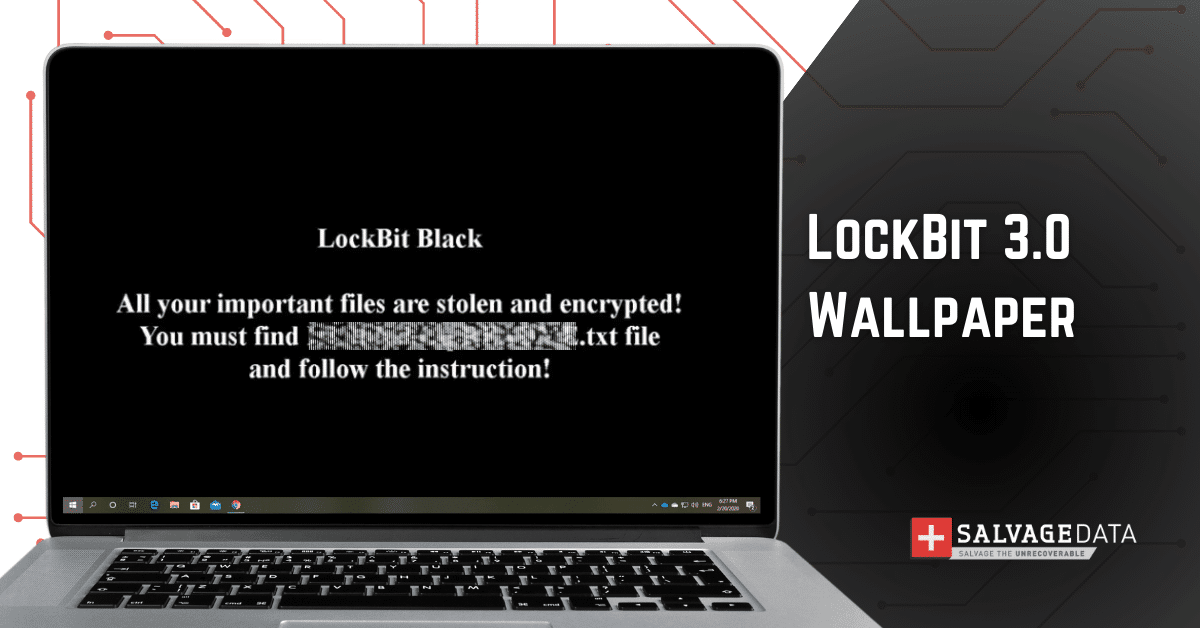
LockBit 3 ransomware, also known as LockBit Black, is a variant of the LockBit ransomware. It encrypts the files and changes their name to a mix of letters, modifies the files’ extension, and also changes the desktop wallpaper. Plus, the LockBit Black ransomware adds a text file to the desktop named [random_string].README.txt.
It’s a dangerous ransomware that is growing its activities and infecting more systems each day. In Q4 2022, LockBit 3 alone was responsible for 21% of ransomware attacks, totalizing 40 incidents.
It’s believed that LockBit 3.0 hackers work with global affiliates. One of the LockBit variants is known for targeting VMware ESXi servers (LockBit ESXi) while the group recently started targeting macOS as well.
What kind of malware is LockBit 3.0?
LockBit 3.0 is ransomware which is a type of malware that encrypts and locks the victims’ files and then requests a ransom in exchange for the decryption key.
LockBit 3.0 is the newest version of LockBit ransomware, first discovered in March 2022, and is used by cybercriminals to conduct extortion attacks on unsuspecting victims. It is more modular and evasive than previous versions and shares similarities with BlackMatter and other ransomware families.
Once LockBit 3.0 executes on a system, it will automatically vet the system for files to encrypt and modify their filenames with an extension like .lockbit or .lockedbit in the Linux variant. In contrast, on the Windows variant, the extension is a mix of characters. It will then display a ransom note demanding payment from the victim in order for them to regain access to their data.
Identify LockBit 3 ransomware
You can recognize the LockBit 3 through a few symptoms and signs on your computer. As soon as you realize you are a victim of a cyber attack, contact local authorities immediately and disconnect your computer from the internet as well as remove any device from your computer (like external SSD or flash drives).
Confirmed Name
- LockBit 3.0 virus
Threat Type
- Ransomware
- Crypto Virus
- Files locker
Encrypted Files Extension
- Randomly generated extension
Ransom Demanding Message
- [random_string].README.txt
Is There a Free Decryptor Available?
- No, there’s no public decryption key for LockBit 3
Detection Names
- Avast Win32:CrypterX-gen [Trj]
- Emsisoft Gen:Trojan.Heur.UT.kuW@aG4Vbyc (B)
- Kaspersky UDS:Trojan.Multi.GenericML.xnet
- Malwarebytes Ransom.LockBit
- Microsoft Trojan:Win32/Casdet!rfn
- Sophos Troj/Lockbit-F
Symptoms
- Cannot open files stored on your computer
- New file extensions
- A ransom demand message on your desktop
- Files renamed with random letters
Ransomware family, type & variant
- Lockbit 3.0 is also known as LockBit Black
- It is part of the LockerGoga & MegaCortex malware family
- It is a new variant of the LockBit ransomware
- This is a BlackMatter ransomware type
Distribution methods
- Infected email attachments (phishing emails)
- Torrent websites (infected links or files)
- Malicious ads (malvertising)
Consequences
- Locked files
- Stolen passwords
- Data breach
Prevention
- Antivirus and anti-malware
- Updated software
- Updated operating system (OS)
- Firewalls
- Don’t open an email attachment from an unknown source
- Do not download files from suspicious websites
- Don’t click on ads unless you’re sure it’s safe
- Only access websites from trustworthy sources
LockBit 3.0 ransomware malicious domains:
- https://www.premiumize[.]com
- https://anonfiles[.]com
- https://www.sendspace[.]com
- https://fex[.]net
- https://transfer[.]sh
- https://send.exploit[.]in
- *http://lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead.onion/
*Hacker group domain accessible only via Tor browser.
How did LockBit 3 infect your computer
As with any cyberattack, LockBit 3 has many ways to enter your system and both steal and lock your data. Most of the time, human error is responsible for the infection.
For example, when you or an unaware employee click on an email link or download its attachment. Many hackers use phishing emails that pose as legit to deceive victims and convince them to click the attachment. A good way to avoid these emails is by using an email provider that blocks malicious emails from reaching you. Also, look for grammar errors, not only typos. Most fake emails have grammar eros that you can easily spot.
Pirate files and software also can be the gateway for ransomware. Besides, pirating movies, music, and software are illegal and ethically reprehensible.
One more way LockBit 3 attacks happen is through unsecured external remote services. Attackers will exploit Remote Desktop Protocol (RDP) tool whose credentials are known, reused, weak, or rephrase to gain access to businesses’ networks and leak data.
Hackers use software with known vulnerabilities to attack businesses as well. That’s why it’s very important to also keep every software updated and protect remote administration tools like RDP.
LockBit 3 encryption and ransom note
The LockBit 3 ransom note not only states that data is stolen and encrypted but also warns that if victims do not pay the ransom, the attacker group will publish the data on the darknet (on a Tor website).
The text also instructs to contact the attackers using the provided websites and a personal ID.
After you are hit by LockBit 3 ransomware, you can see the following letter as a text file on your desktop:
~~~ LockBit 3.0 the world’s fastest and most stable ransomware from 2019~~~
>>>>> Your data is stolen and encrypted.
If you don’t pay the ransom, the data will be published on our TOR darknet sites. Keep in mind that once your data appears on our leak site, it could be bought by your competitors at any second, so don’t hesitate for a long time. The sooner you pay the ransom, the sooner your company will be safe.
Do not pay the ransom. Besides being illegal, paying the ransom has serious consequences such as sanctions, besides having the moral and ethical issue of financing criminal activity. Paying the ransom doesn’t guarantee you will get the key or that it will work.
How does LockBit 3 work
The LockBit 3 ransomware acts in three stages: exploit, infiltrate, and deploy.
1. Exploit
The first stage is to exploit weaknesses in the network. Any vulnerability, such as open RDP and not updated security software is a gateway for cyberattacks.
Also, phishing emails and malvertising are other ways cyber attackers exploit vulnerabilities.
2. Infiltrate
In this stage, the LockBit 3 will infect any other machine connected. Therefore, remove any device connected to the infected machine and unclog it from the internet to restrain the malware.
It will spread through the network via lateral movement and achieve an attack-ready level of access.
During the infiltration phase, LockBit 3 actors gather information, escalate privileges, moves laterally in the network, and exfiltrate data.
3. Deploy
During this stage, LockBit 3.0 deletes any restore points, and backups, stops specific services, and then it starts to lock and encrypt every file. LockBit 3 is one of the fastest ransomware available and will encrypt your data very quickly.
The goal is to make recovery impossible or to delay it, causing long downtime that can damage your business reputation and even ruin it.
At this point, you can see both the ransom note and the wallpaper. Now it’s time to decide if you’re going to follow the criminals’ demands (which are not recommended) or follow the steps to securely recover your encrypted files.

Prevent LockBit 3 ransomware attack
We already mentioned several ways you can prevent LockBit 3 ransomware attacks. Here is a complete list of what to do to keep your data and business safe.
You can prevent ransomware by eliminating weaknesses. To do so you can keep all software updated and create cybersecurity awareness by training your team on cyber threats.
1. Use strong passwords
Always use strong and unique passwords for each account and only share them with necessary people. For example, if an employee doesn’t require a website account or software for their work, they don’t need access to it. This can guarantee that only authorized personnel will access each company account.
2. Apply multi-factor authentication
You can use two-factor authentication or biometric unlock to ensure that only authorized people have access to folders, devices, or accounts.
3. Erase outdated and unused user accounts
Unused accounts are vulnerabilities that hackers can exploit. Deactivate and close unused accounts as well as those used by past employees.
4. Keep software updated
As mentioned, outdated software is a weak point. That’s because new updates can create protection against new types of malware, such as LockBit 3.
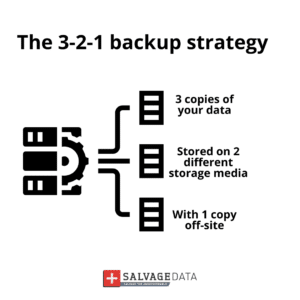
5. Schedule regular backups
Keep at least three copies of your data, having at least one stored offline and off-site. This can guarantee that, even if you’re hit by a disaster, being natural or human-made (like ransomware), your data is always safe.
Regular backups can prevent downtimes and ensure you never lose any sensitive data.
6. Use a cybersecurity solution
You can either have an IT team to guarantee your business security or hire a cybersecurity service.
Either way, you must look for vulnerabilities in the network, such as back doors, exploit kits, and youtube software.
7. Have a recovery plan in hand
Data recovery plans are documents that work as guides on what to do in case of a disaster. This can help you restore your business faster and more securely.
See how to create a data recovery plan with our in-depth guide.
How to handle from LockBit 3 attack
The first step to recover from the LockBit 3 attack is to isolate the infected computer by disconnecting from the internet and removing any connected device. Then, you must contact local authorities. In the case of US residents and businesses, it is the local FBI field office and the Internet Crime Complaint Centre (IC3).
To report a ransomware attack you must gather every information you can about it, including:
- Screenshots of the ransom note
- Communications with LockBit 3.0 actors (if you have them)
- Sample of an encrypted file
You must also investigate the extension of the ransomware on your network. To do so you can create a forensic investigation and see if any data was exfiltrated. A ransomware recovery service can help you with this investigation.
You must not delete the ransomware, and keep every evidence of the attack. That’s important for digital forensics so experts can trace back to the hacker group and identify them. Is using the data on your infected system so that authorities can investigate the attack and find the responsible. A cyber attack investigation is not different from any other criminal investigation: it needs evidence to find the attackers.
After isolating the device and contacting authorities, you must follow the next steps to retrieve your data:
1. Contact your Incident Response Retainer
A Cyber Incident Response is the process of responding to and managing a cybersecurity incident. An Incident Response Retainer is a service agreement with a cybersecurity provider that allows organizations to get external help with cybersecurity incidents. It provides organizations with a structured form of expertise and support through a security partner, enabling them to respond quickly and effectively in the event of a cyber incident.
An incident response retainer offers peace of mind to organizations, offering expert support before and in the aftermath of a cybersecurity incident. The specific nature and structure of an incident response retainer will vary according to the provider and the organization’s requirements. A good incident response retainer should be robust but flexible, providing proven services to enhance an organization’s long-term security posture.
2. Identify the ransomware infection
You can check which ransomware infected your machine by the file extension (some ransomware uses the file extension as their name), or it will be on the ransom note. With this information, you can look for a public decryption key. However, LockBit 3 doesn’t have it yet.
3. Remove the ransomware and eliminate exploit kits
Before recovering your data, you must guarantee that your device is ransomware-free and that the attackers can’t make a new attack through exploit kits or other vulnerabilities. A ransomware removal service can delete the ransomware, create a forensics document for investigation, eliminate vulnerabilities, and recover your data.
4. Use a backup to restore the data
Backups are the most efficient way to recover data. Make sure to keep daily or weekly backups, depending on your data usage.
5. Contact a ransomware recovery service
If you don’t have a backup or need help removing the ransomware and eliminating vulnerabilities, you should contact a data recovery service.
SalvageData experts can safely restore your files and guarantee Clop ransomware does not attack your network again.
SalvageData experts can safely restore your files and guarantee LockBit 3 ransomware does not attack your network again. Contact our experts 24/7 for emergency recovery service or find a recovery center near you.













